Overview of selected scams - OCTOBER 2023

We present the report on identified threats and the methods of operation by criminals for the month of October 2023. This document highlights selected risks to customers of Polish banks. We encourage you to review the material.
The document does not include threats already known for many months and described in an earlier report, such as the "classicscam". It is essential to remember, however, that these scenarios are still being used by criminals, and we must continually work against them.
False investments schemess
In October 2023, advertisements on Facebook were still being used to distribute phishing sites. In this way, criminals impersonated well-known clothing stores, offering the chance to obtain a ZTM card, and also carried out other elements of a scenario known as "investment fraud". All of these have been described below.
This is a scheme of fraud in which cybercriminals impersonate well-known individuals or institutions. They aim to persuade potential victims to invest funds with the promise of high returns. Increasingly, criminals in fake offers use themes related to artificial intelligence.
- fake offers were distributed through:
- advertisements on the Facebook platform,
- advertisements in the Google search engine,
- advertisements in the MSN search engine,
- advertisements on social networking site X - Twitter (a new method of distributing fake ads).
After clicking on a link, the client lands on a page where they enter personal data. Then, cybercriminals make telephone contact. The next step is the theft of money from the bank account. Recently, scammers have expanded this scheme. In the published fake ads, they offered help in recovering funds to people who had been cheated in the past. All this to steal money again.
Examples of false advertisements and phishing sites (Fig. 1-4):
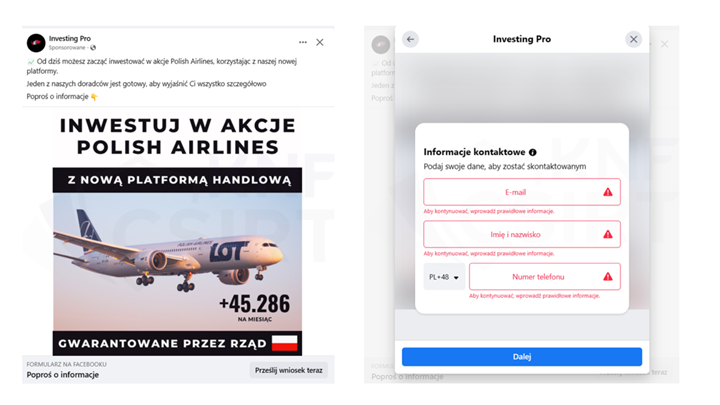
Figure 1 Impersonation of LOT - the national airline od poland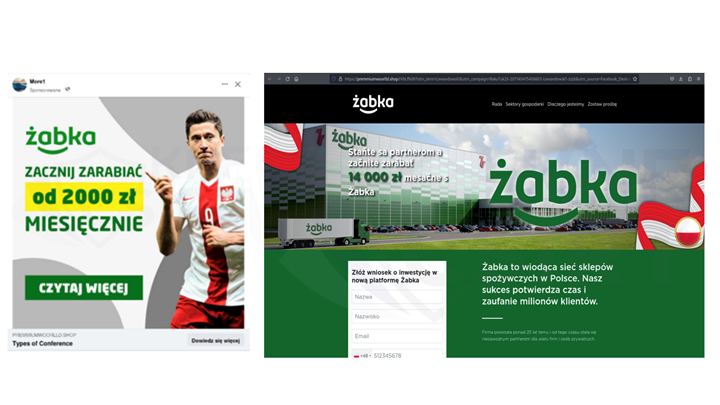
Figure 2 Impersonation of Żabka - a popular chain of convenience stores in poland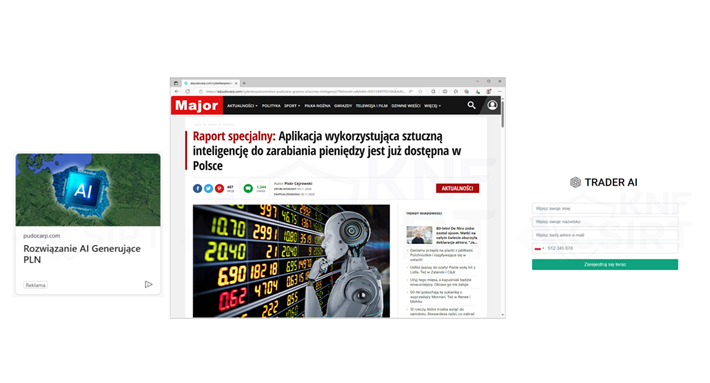
Figure 3 Impersonation of Trade AI
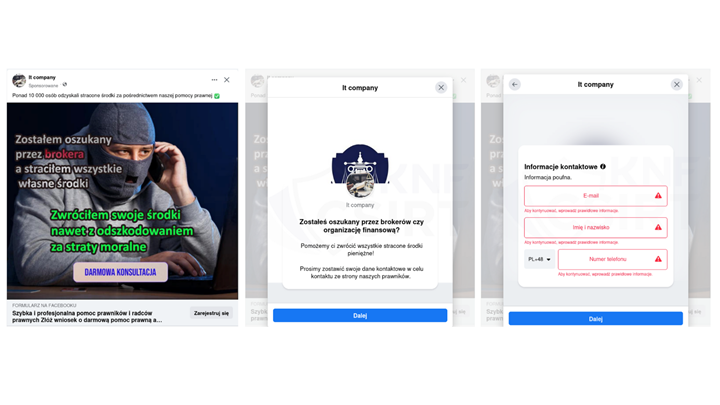
Figure 4 Help in recovering lost funds
Price deals
Cybercriminals offered products at competitive prices. On phishing sites, they impersonated the MOHITO, CROPP, EOBUWIE, and SINSAY stores. Upon entering the site, the victim had to fill out a personal form. Then, the victim was asked to enter payment card details. All the data went into the hands of the criminals.
Advert on the Facebook platform, containing a phishing page (Fig. 5-8):
Figure 5 Advertisement on Facebook - impersonation of the MOHITO store

Figure 6 Advertisement on Facebook - impersonation of the CROPP store
Figure 7 Advertisement on Facebook - impersonation of the EOBUWIE store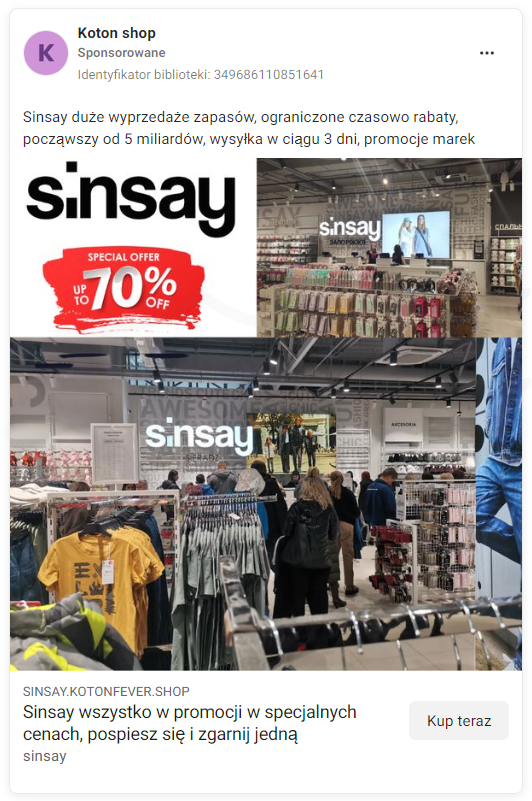
Figure 8 Advertisement on Facebook - impersonation of the SINSAY store
Phishing pages (Fig. 9-11):
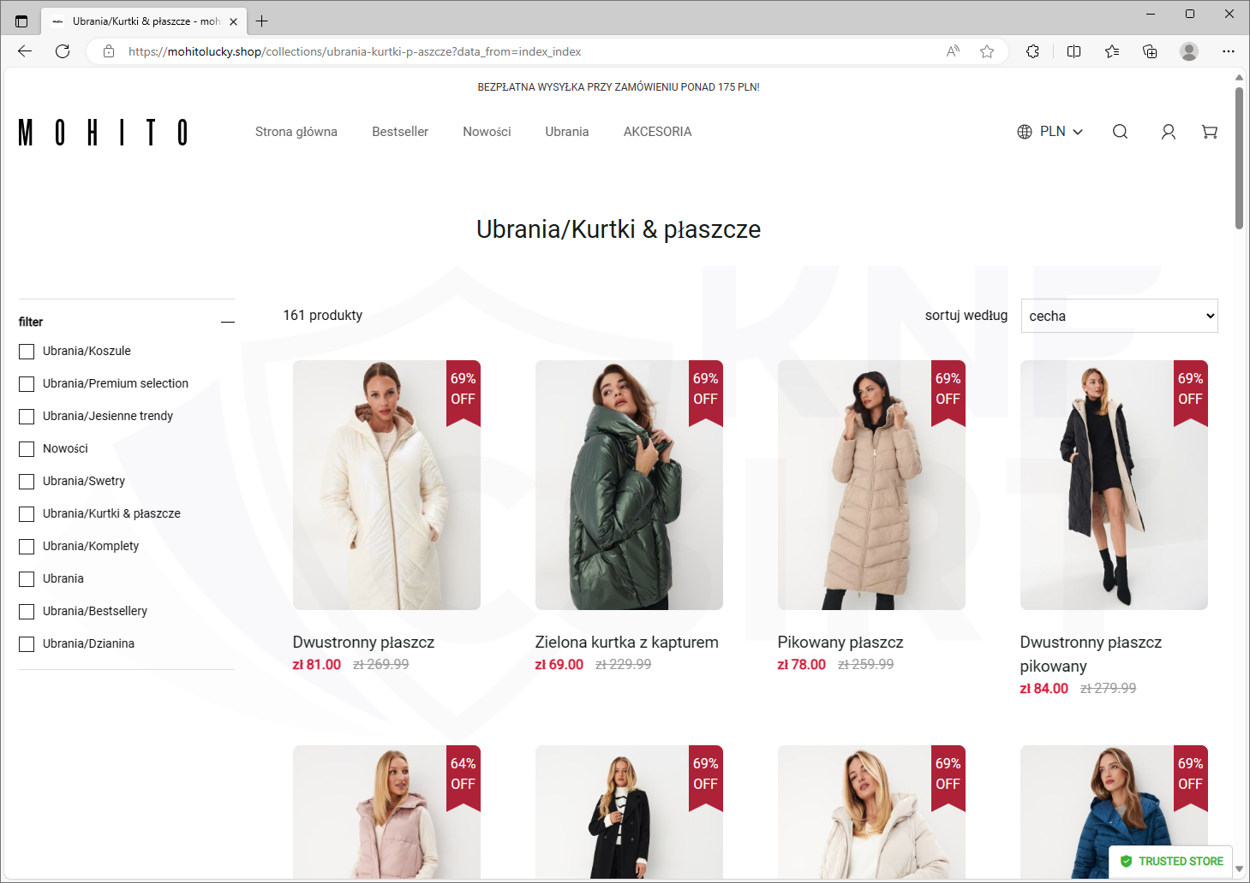
Figure 9 Fake shop site 1/3
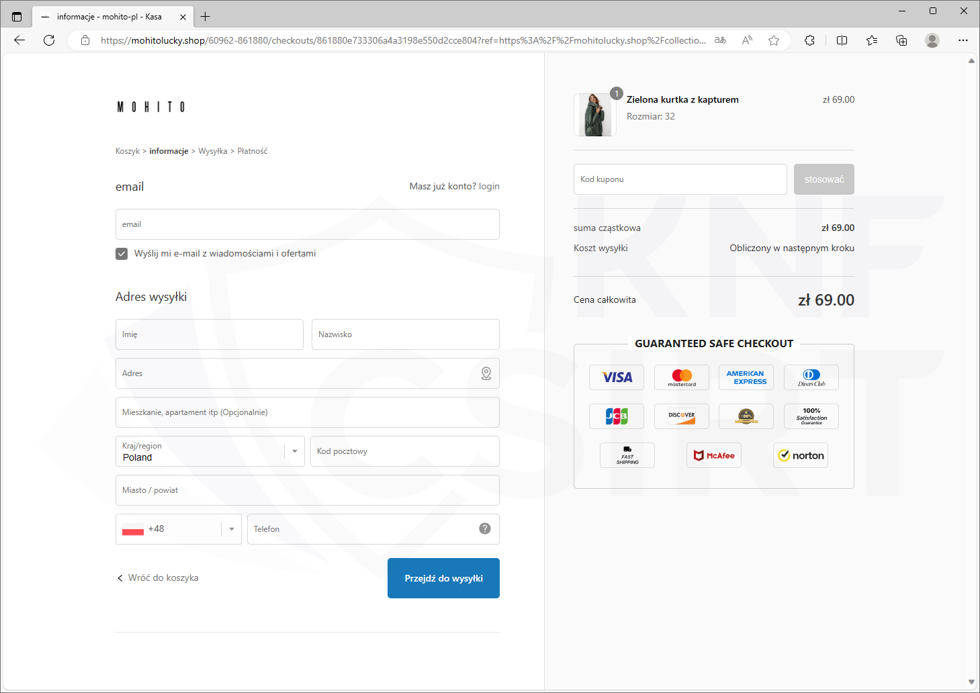
Figure 10 Fake shop site 2/3
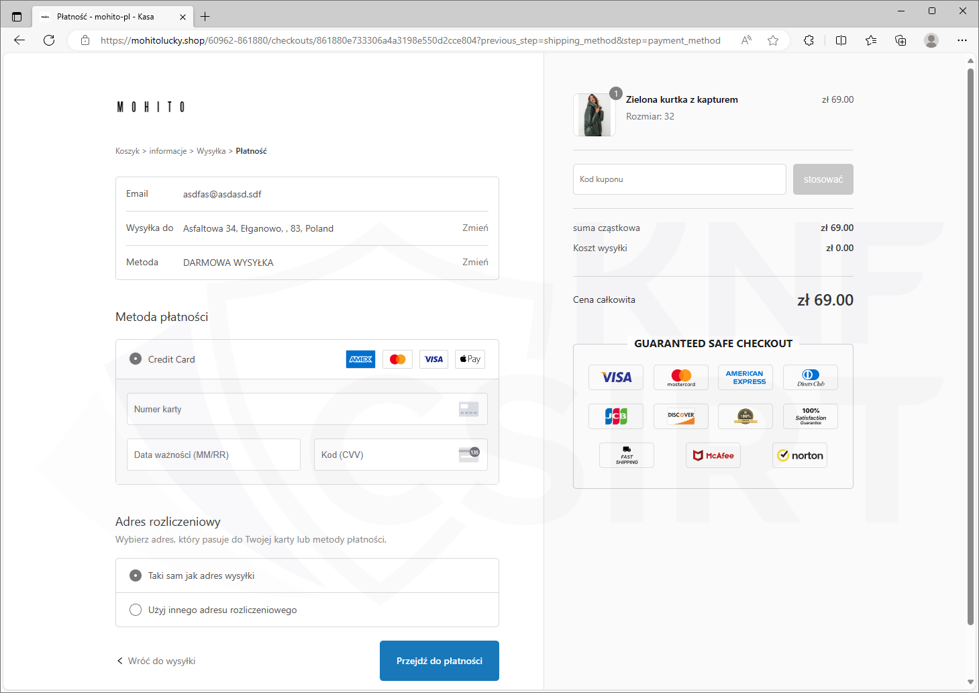
Figure 11 Fake shop site 3/3
Sales of lost luggage
Cybercriminals, impersonating LOT, announced a supposed opportunity to purchase lost luggage. After clicking on an ads on Facebook, the victim was directed to a phishing site. On this site, entering payment card information was required.
Advert on the Facebook platform, containing a phishing page (Fig. 12):
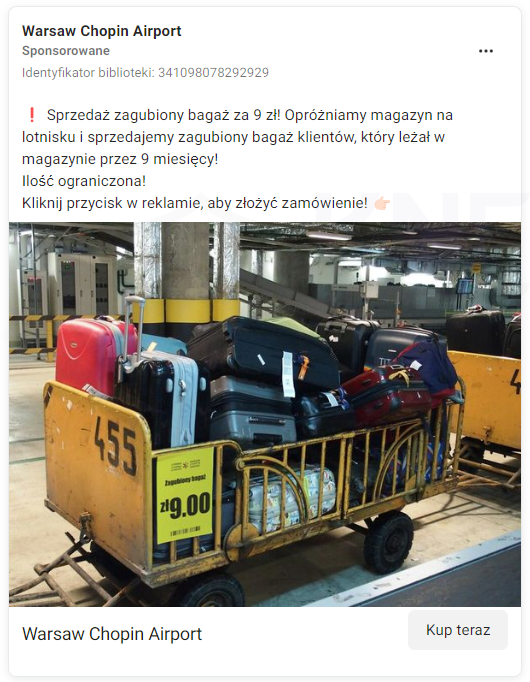
Figure 12 Advertisement on Facebook - sale of lost luggage
Phishing page (Fig. 13):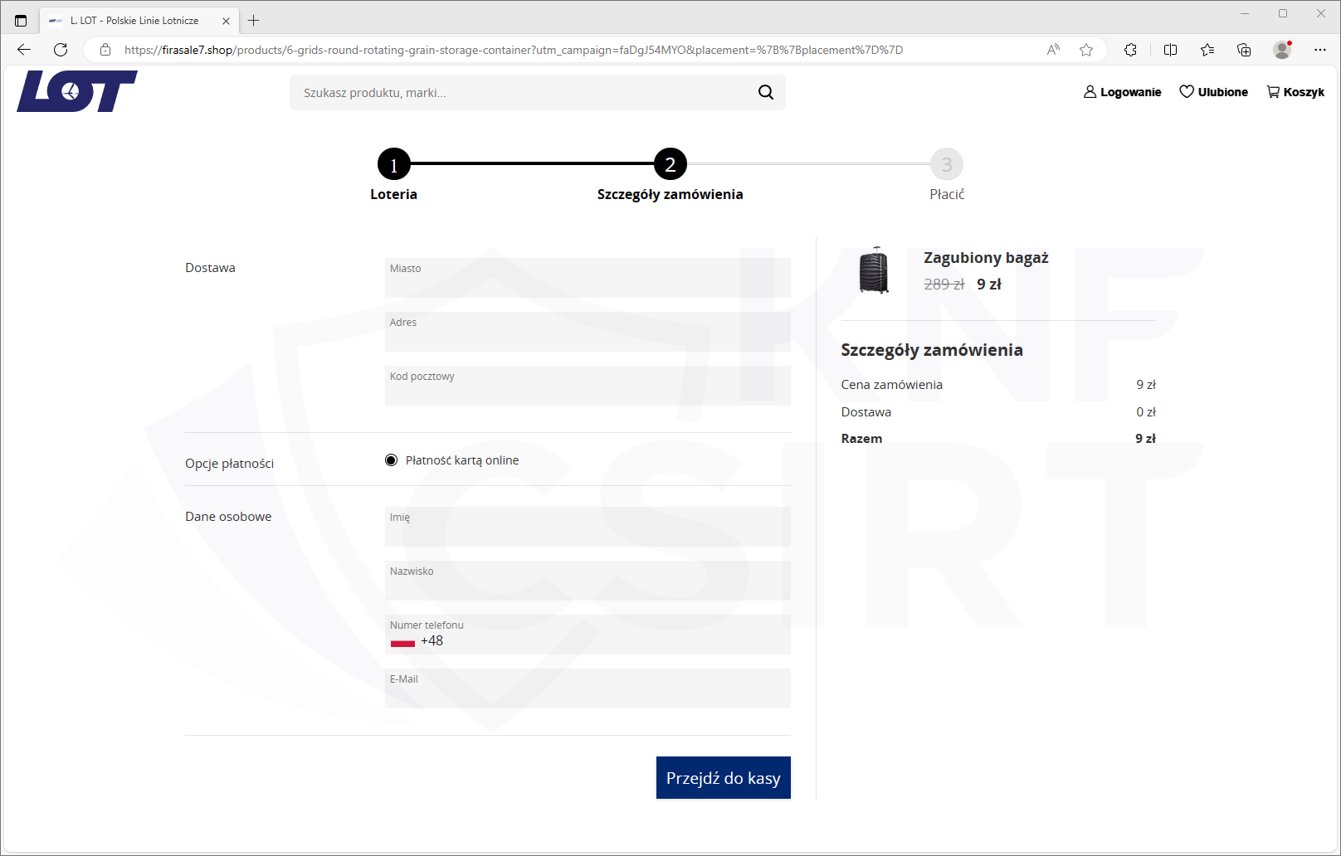
Figure 13 Phishing site impersonating LOT
Receive ZTM card
Cybercriminals, impersonating ZTM (the Warsaw Public Transport Authority), announced a supposed opportunity to obtain a card that would entitle users to public transport rides. This card was advertised for sale at a very attractive price. After clicking on a link from the advertisement, the victim landed on a phishing site. There, they were presented with information about a supposed lottery. Subsequently, the victim was asked to enter their personal details and payment card information.
Advert on the Facebook platform, containing a phishing page (Fig. 12):

Figure 14 Advertisement on Facebook - ZTM card
Phishinge pages (Fig. 15-17):
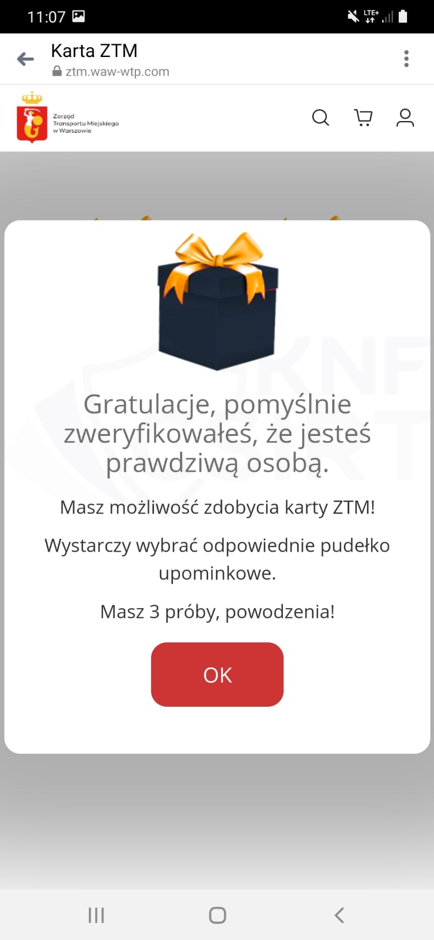
Figure 15 Phishing site impersonating ZTM 1/3
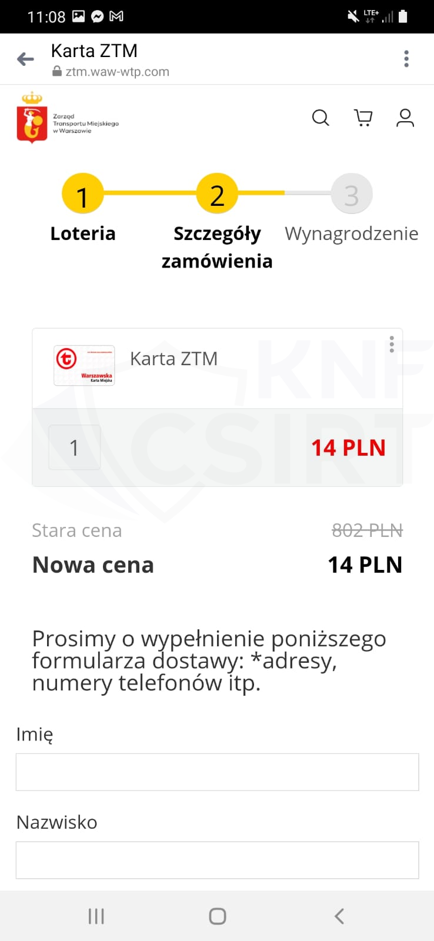
Figure 16 Phishing site impersonating ZTM 2/3
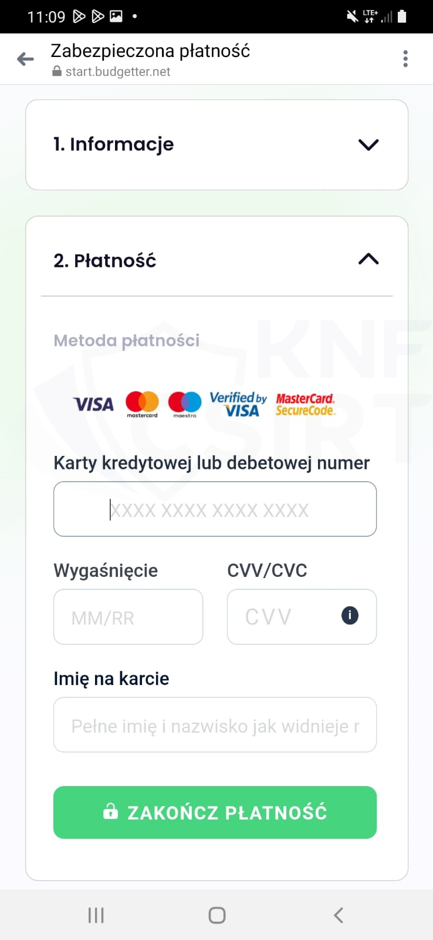
Figure 17 Phishing site impersonating ZTM 3/3
Sensational news on Facebook
Cybercriminals published fake posts on Facebook containing sensational news. Upon clicking on the post, the user was directed to a page with a fake article. To access the content, the victim had to confirm their age of majority. To do this, they were asked to enter their Facebook login details. Subsequently, the criminals would take over their account. The cybercriminals then impersonated the victim, publishing compromising content and sending messages to their friends to extort money.
Fake post on Facebook portal (Fig. 18):
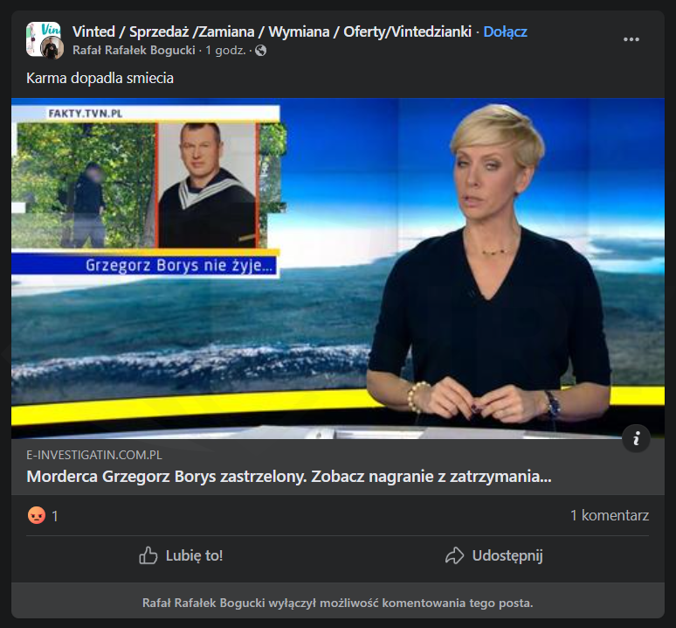
Figure 18 Fake post on Facebook containing sensational information
Phishing page (Fig. 19):
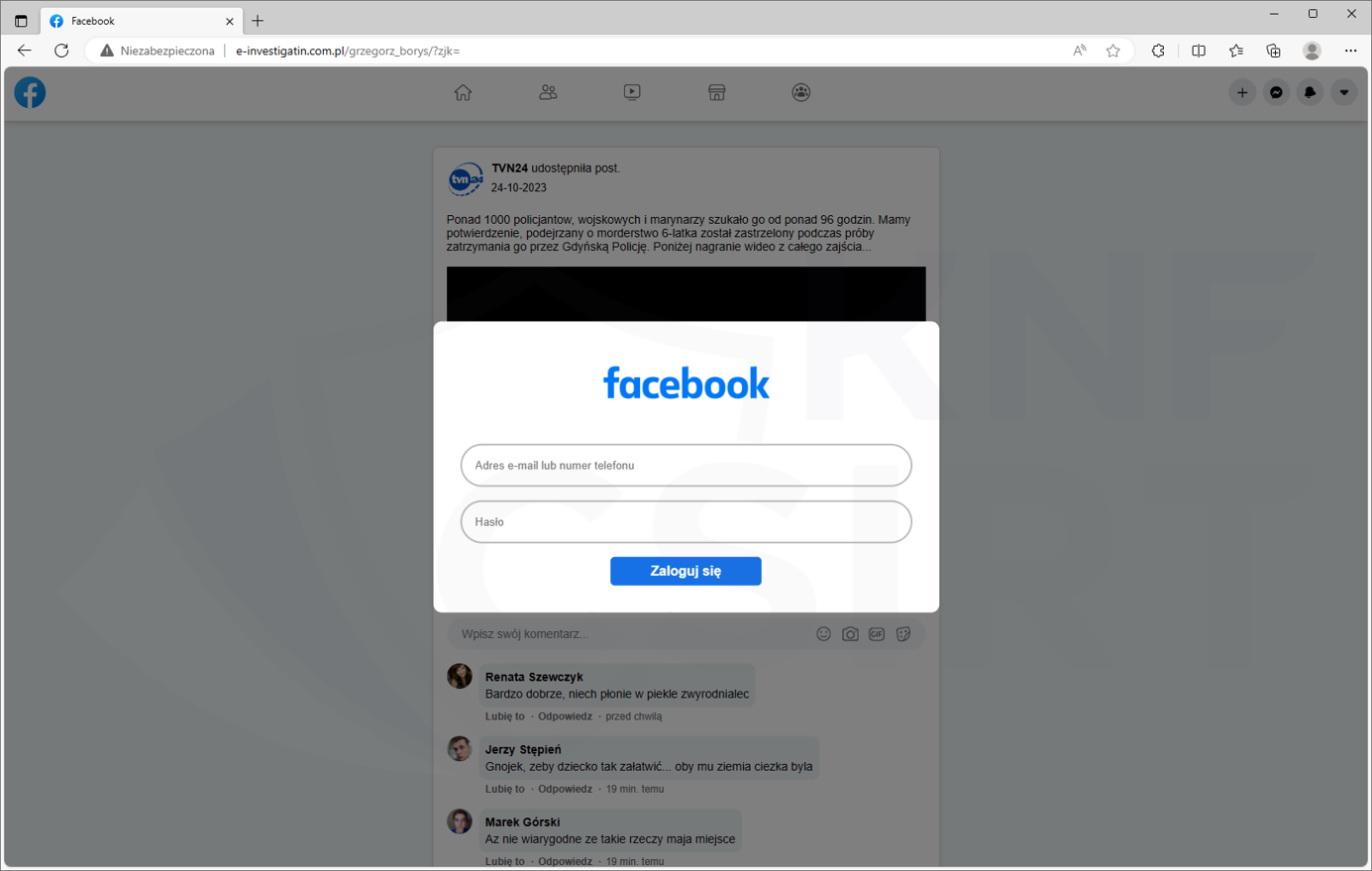
Figure 19 Phishing site impersonating Facebook
Fake SMS messages
A well-known method for distributing phishing domains for years has been SMS messages. In October 2023, it was still one of the main methods.
Impersonation of ING Bank Śląski
Cybercriminals impersonating ING bank sent out SMS messages. They informed that access to the banking app had been blocked. This, of course, was a lie. Clicking on the link in the message led the victim to a phishing site. If they entered their online banking login details there, the criminals would then gain access to this information.
SMS message containing a phishing site (Fig. 20):
Figure 20 Fake SMS message impersonating ING Bank Śląski
Phishing pages (Fig. 21-23):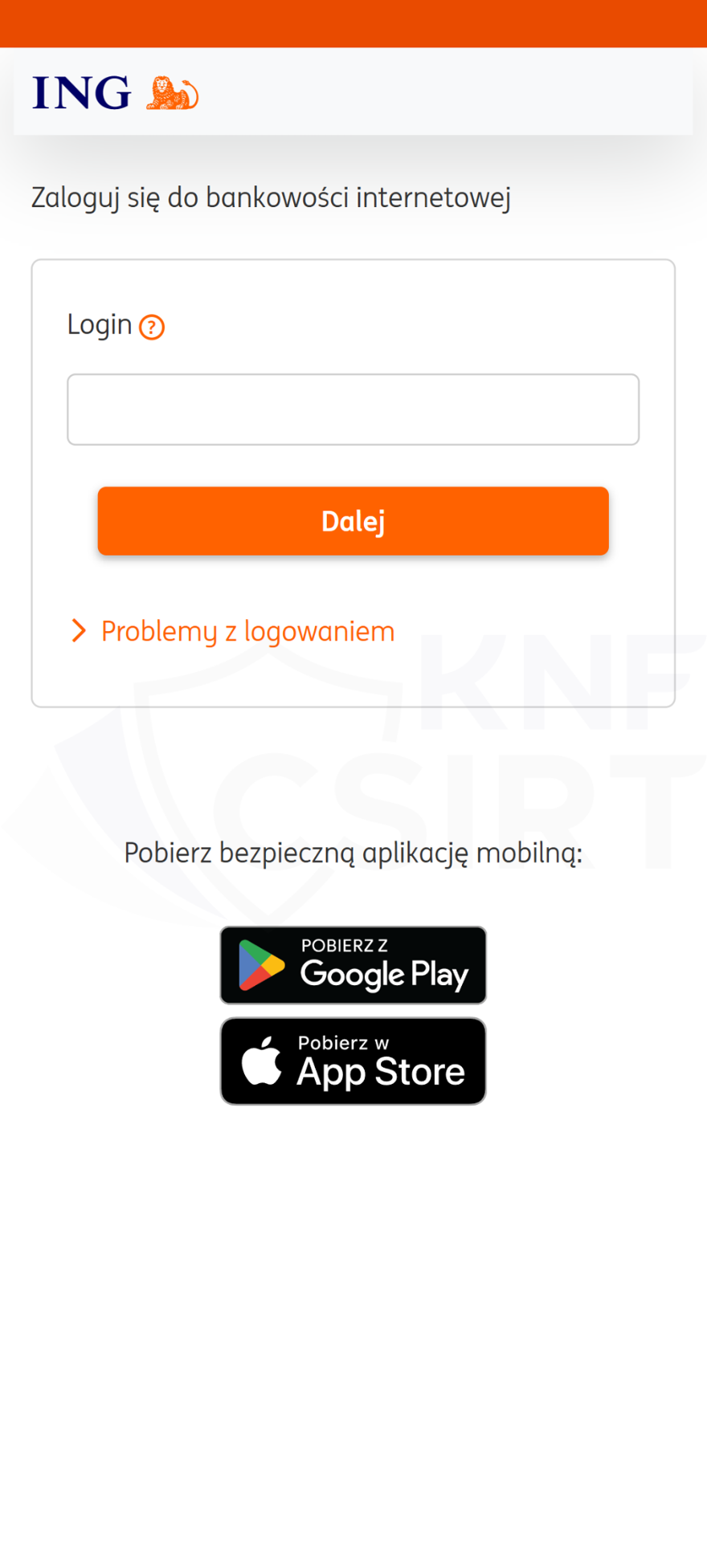
Figure 21 Phishing site impersonating ING Bank Śląski 1/3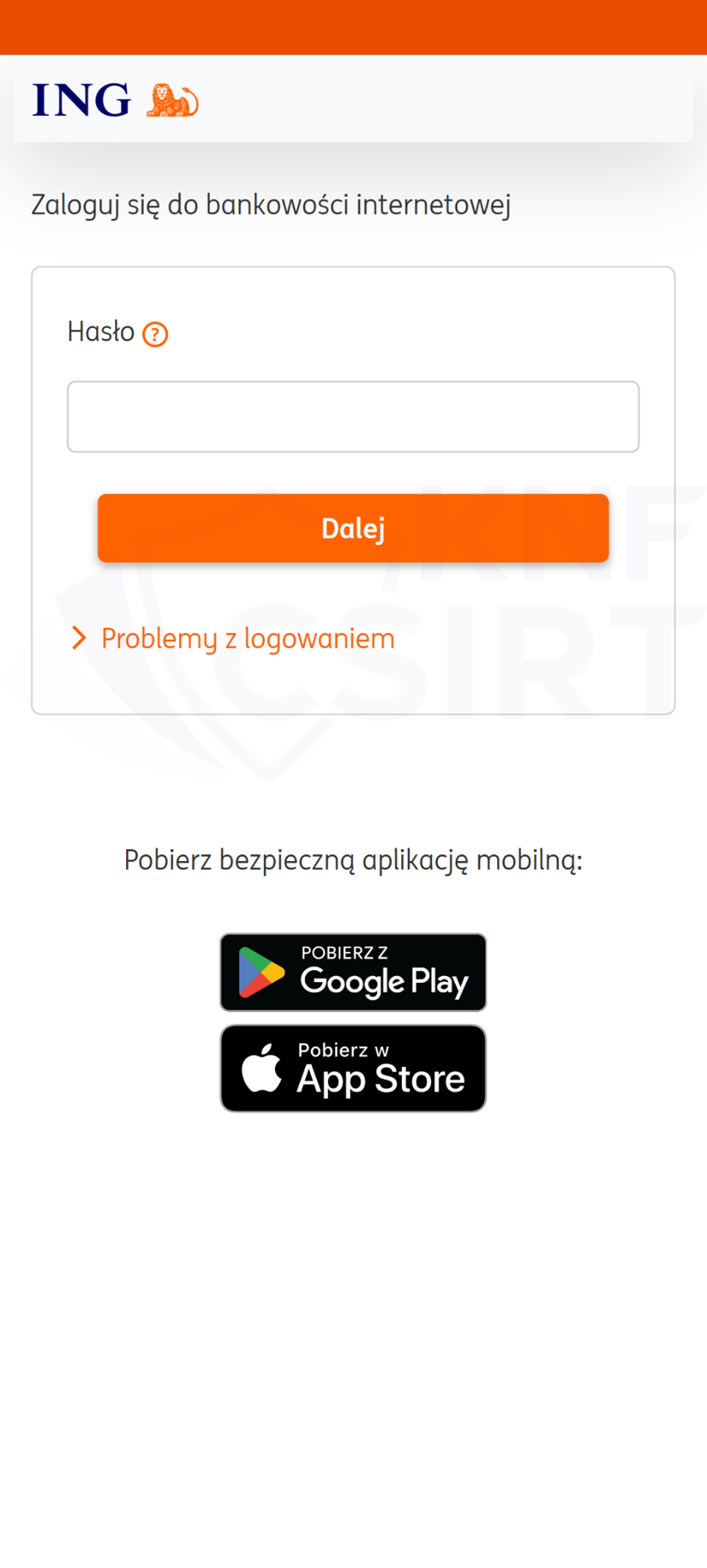
Figure 22 Phishing site impersonating ING Bank Śląski 2/3
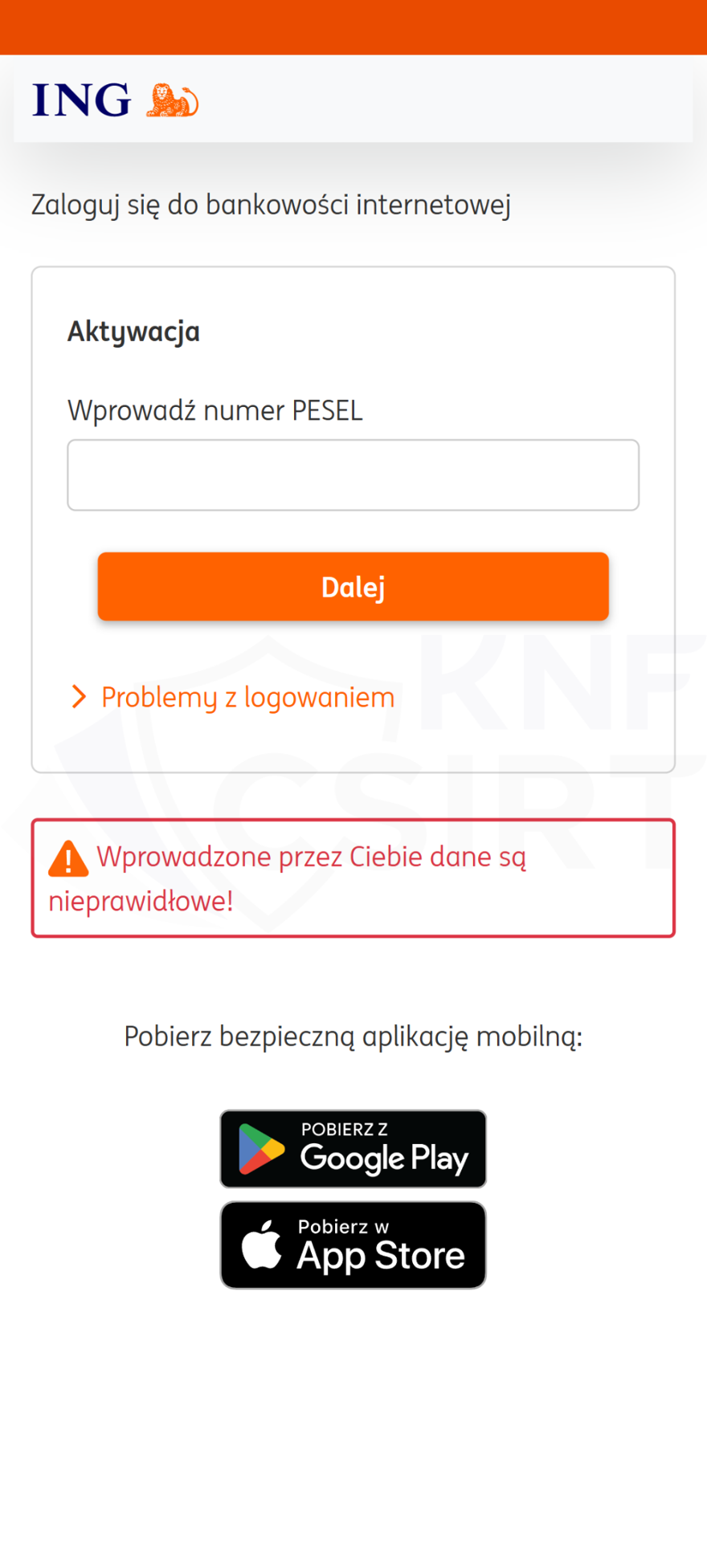
Figure 23 Phishing site impersonating ING Bank Śląski 3/3
Phishing campaign impersonating Polish Post Office
In October 2023, cybercriminals continued to impersonate Polish Post Office (Poczta Polska). This time, they sent SMS messages informing recipients about customs duties. The message contained a phishing link. Clicking on the link led the victim to a page where they were encouraged to enter their personal information and payment card details (full number, expiration date, CVV code), along with 3DSecure codes. We identified Chinese Threat Actors of phishing panels conducting such a campaign. These groups offer their services through a PhaaS (phishing-as-a-service) model.
Sampe SMS message sent as part of the phishing campaign (Fig. 24):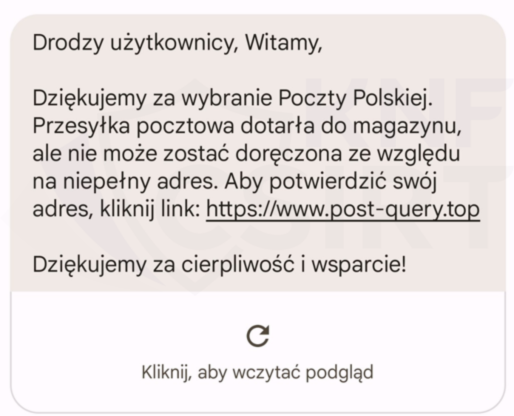
Figure 24 Fake SMS message impersonatin Polish Post
Phishing pages (Fig. 25-27):
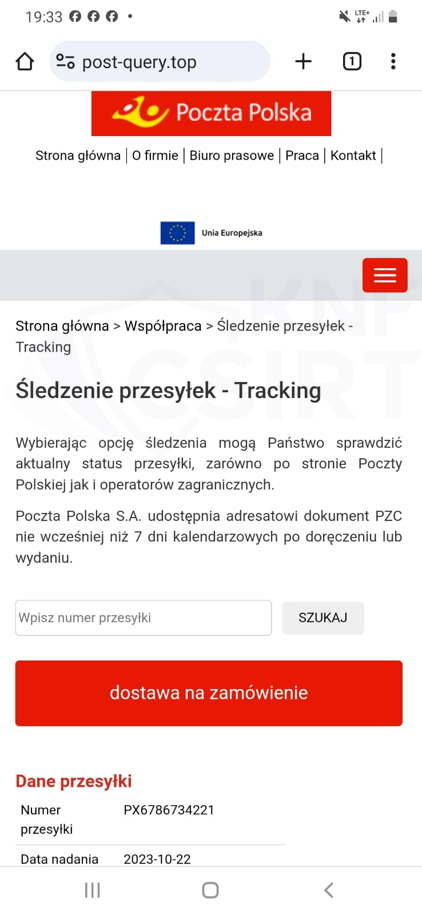
Figure 25 Phishing site impersonating Polish Post 1/3
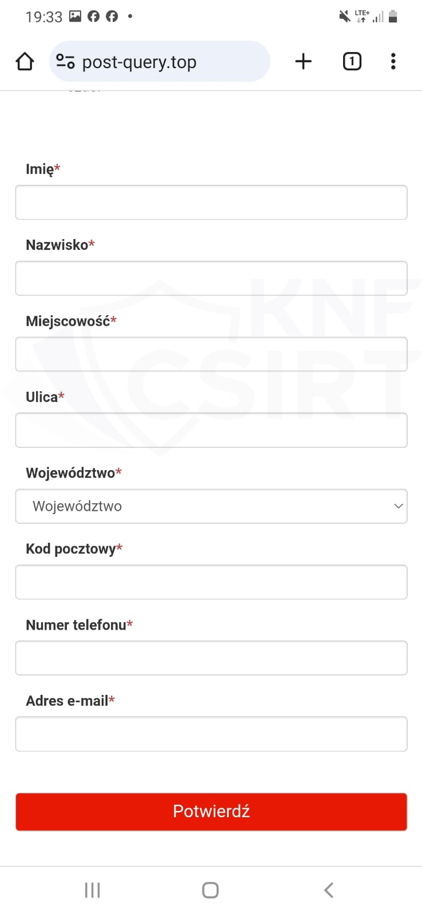
Figure 26 Phishing site impersonating Polish Post 2/3
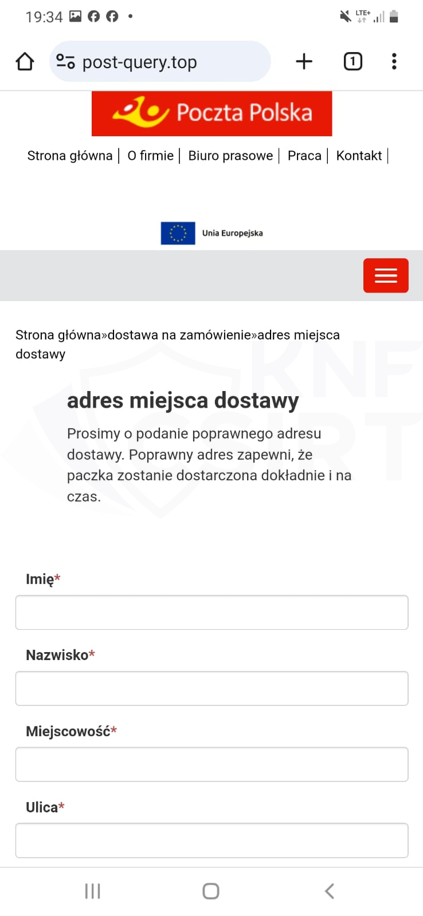
Figure 27 Phishing site impersonating Polish Post 3/3
Impersonation of the courier company - InPost
Cybercriminals impersonating the courier company InPost sent out SMS messages. They informed about the need to update the delivery address. This, of course, was a lie. The message contained a link, and clicking on it led the victim to a phishing site. On this site, payment card details (full number, expiration date, CVV code) and personal data of the victim were stolen.
Sampe SMS message sent as part of the phishing campaign (Fig. 28):
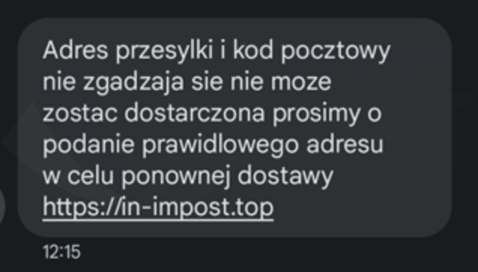
Figure 28 Fake SMS message impersonating of InPost
Phishing pagea (Fig. 29-31):
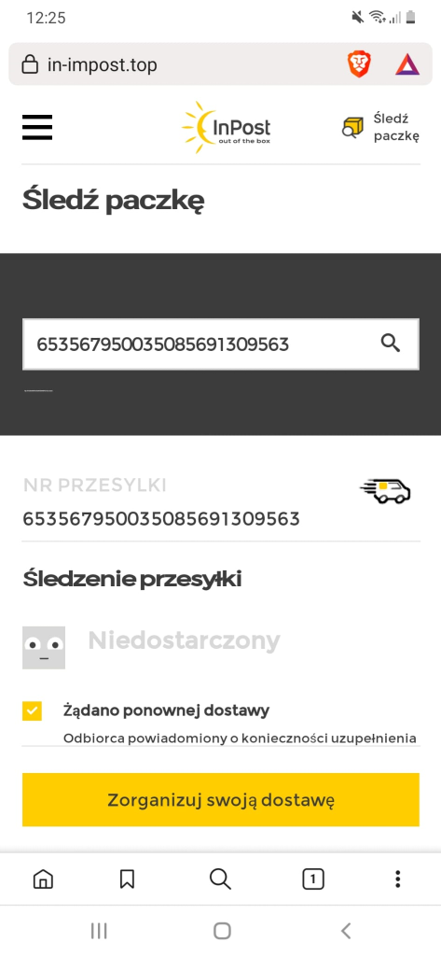
Figure 29 Phishing site impersonating InPost 1/3
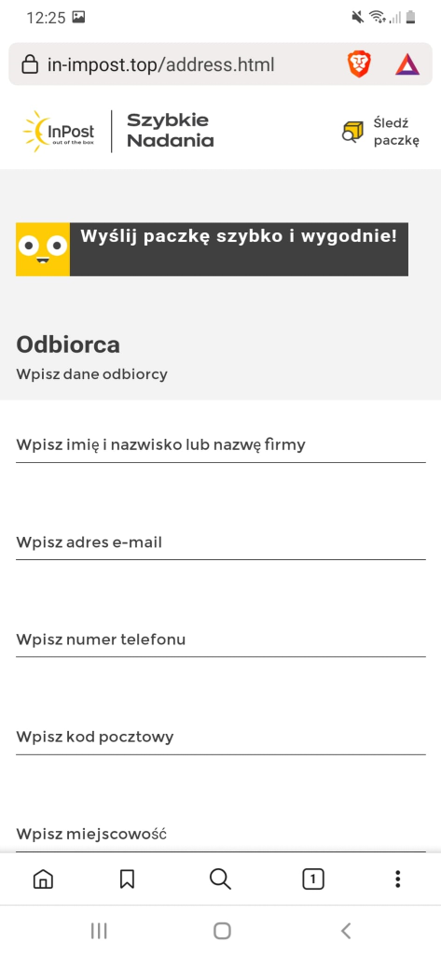
Figure 30 Phishing site impersonating 2/3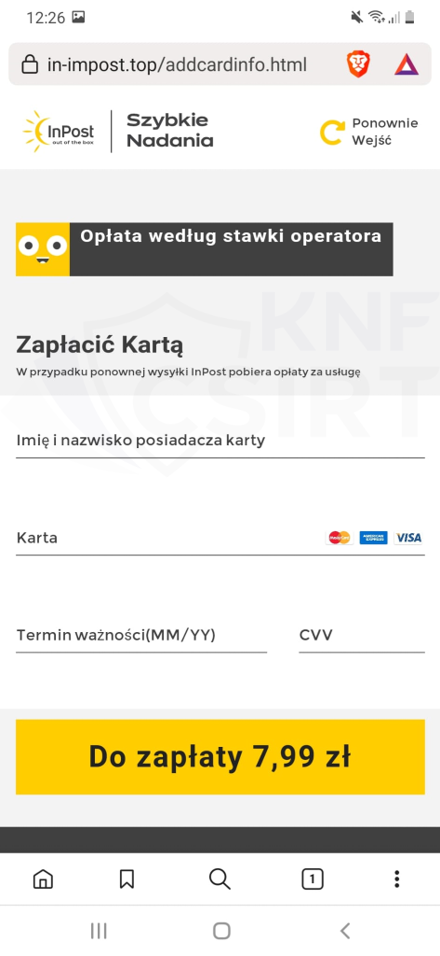
Figure 31 Phishing site impersonating InPost 3/3
Fake e-mail messages impersonating home.pl
Cybercriminals impersonated home.pl, a Polish company offering web hosting, domain registration, and various internet service solutions., They were sending out fake email messages. They informed users about the need to pay for a service, which was, of course, a scam. Clicking on the link in the email led the victim to a dangerous website where payment card details were stolen.
Example of an email message sent as part of a phishing campaign (Fig. 32):
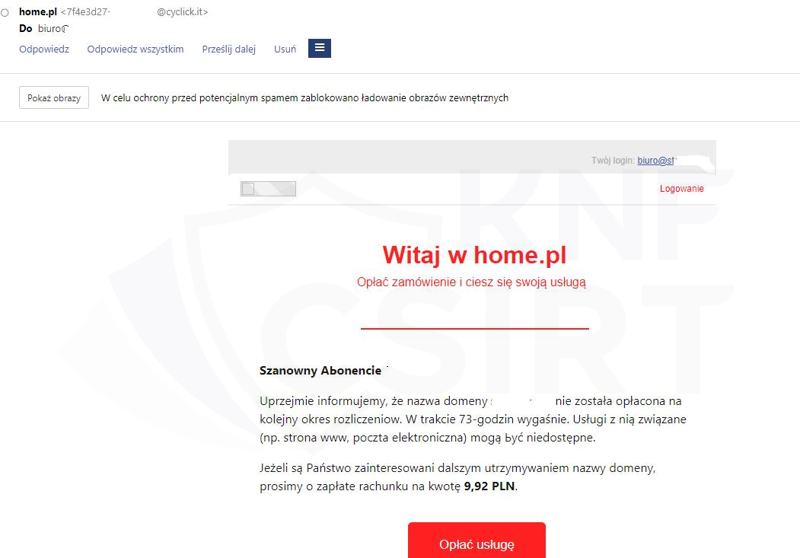
Figure 32 Fake e-mail message impersonating home.pl
Phishing page (Fig. 33):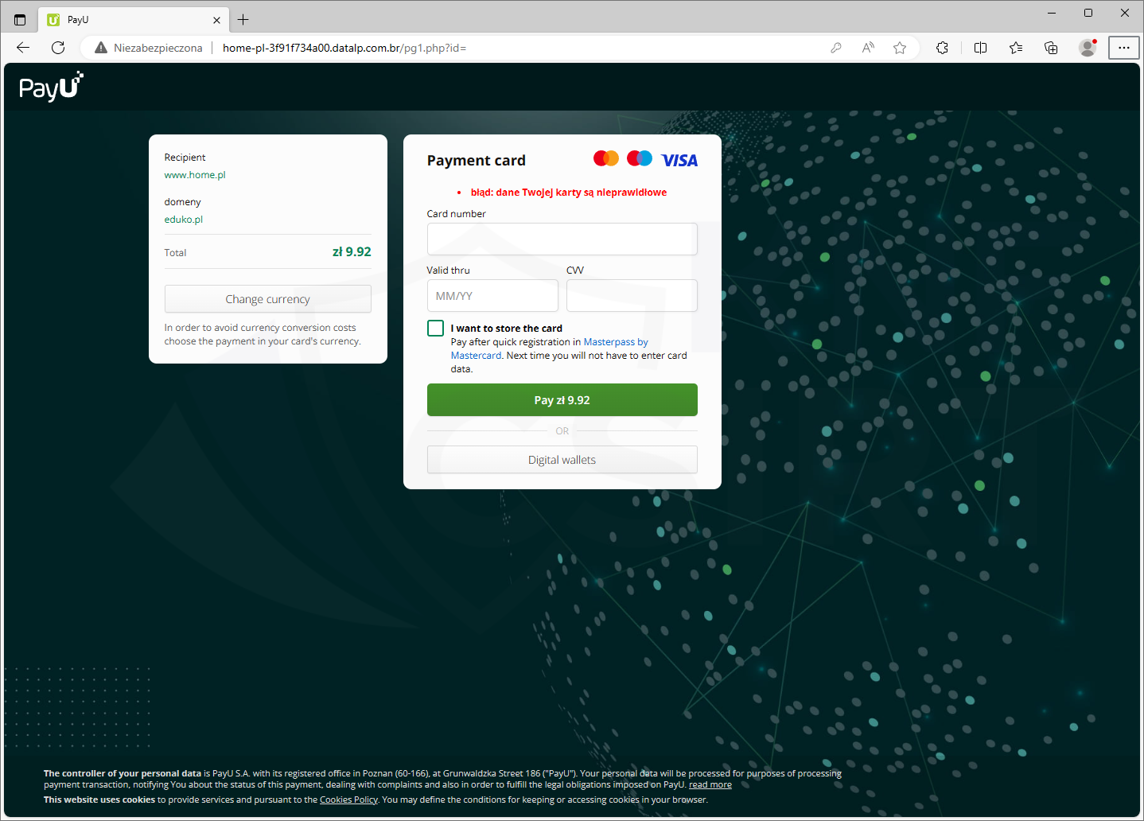
Figure 33 Phishing site impersonating PayU (payment intermediary)
Fake e-mail messages impersonating Netflix
Cybercriminals, impersonating Netflix, sent out fake email messages. They informed recipients about the expiration of their subscription. The message contained a link leading to a page imitating the Netflix service. The criminals aimed to obtain users' payment card details.
Example of an email message sent as part of a phishing campaign (Fig. 34):
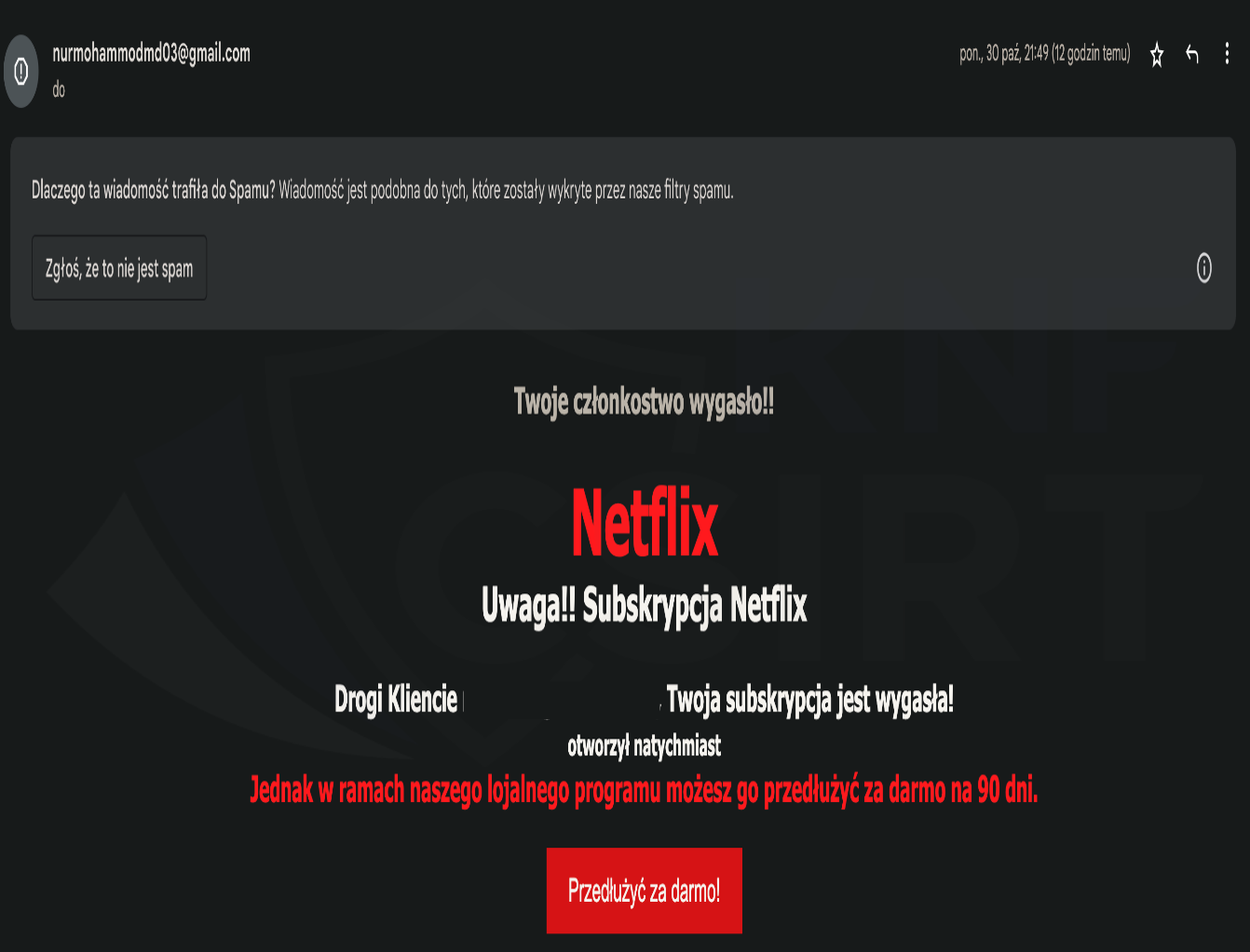
Figure 34 Fake e-mail message impersonating Netflix
Phishing pages (Fig. 35-36):

Figure 35 Phishing site impersonating Netflix 1/2
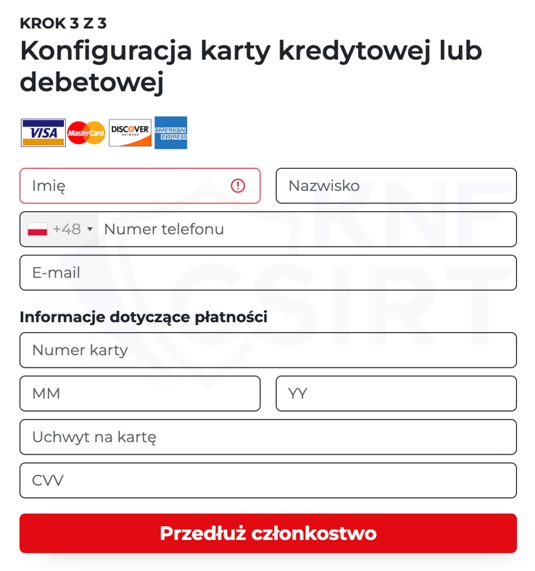
Figure 36 Phishing site impersonating Netflix 2/2
Yet another month of this year has demonstrated that criminals are constantly refining their methods of operation. We consistently believe that conducting informational and educational activities is crucial.
That's why news about cyber threats and fraudulent trends are also published on the following our social media platform: Twitter, LinkedIn and Facebook.

