Overview of selected scams - December 2023

We present the report on identified threats and the methods of operation by criminals for the month of December 2023. This document highlights selected risks to customers of Polish banks. We encourage you to review the material.
The document does not cover threats that have been known for many months and were described in an earlier report, such as the "classicscam", fake Facebook login panels, fake shops and other. It is essential to remember, however, that these scenarios are still being used by criminals, and we must continually work against them.
False investment schemess
In December 2023, the scam known as "investment fraud" was still active. This fraud scheme involves cybercriminals impersonating well-known individuals or institutions, with the aim of persuading potential victims to invest funds in exchange for a high rate of return.
Criminals in fake offers are increasingly utilizing deepfake technology. This allows them to create materials that are even more convincing. They use the likeness of a well-known person and encourage investment using their voice. It's amazing how they have learned to mimic lip movements to match the spoken words.
After clicking on a link, the victim lands on a page where registration is required. It also happens that the form to enter data is located directly on Facebook (Fig. 1).
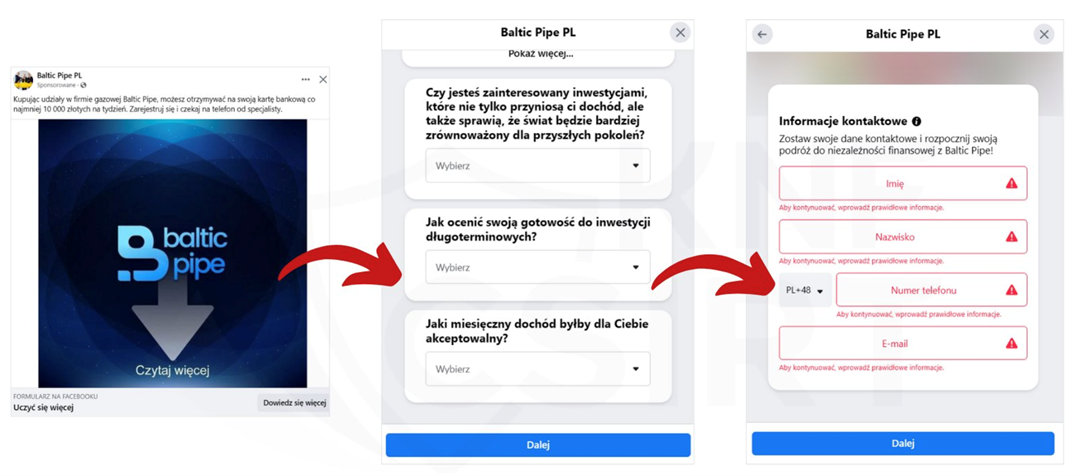
Figure 1 False investment - form on Facebook platform
The data obtained by cybercriminals in this way enables them to contact a potential, already manipulated person, and in the next step to steal their funds. Often, in similar cases, the criminals encouraged the installation of remote management software. And when the victim of this crime wants to withdraw the earned financial resources (often realizing that they may have been deceived), they receive information about the need to "check the bank account through the AML system". For this purpose, cybercriminals send a link to a phishing site, where authentication data for electronic banking are extorted. In this way, cybercriminals first persuade the victim to transfer high amounts, and then gain access to electronic banking. Recently, scammers have expanded their fraud variant. In published fake advertisements, they offered alleged help in recovering funds to people who had already fallen victim to investment fraud earlier. All this in order to play a psychological game and persuade them to hand over further savings.
Examples of false advertisements and phishing sites (Fig. 2):
Figure 2 False investment – ads utilizing the theme of artificial intelligence
Fake SMS messages
A well-known method for distributing phishing domains for years has been SMS messages. In December 2023, it was still one of the main methods.
Impersonating polish Post Office
During the holiday season, we analyzed the intensification of a phishing campaign impersonating Poczta Polska (Polish Post). This scenario has been known for a long time and has been described by us on several occasions.
You can read here: https://cebrf.knf.gov.pl/images/Raporty/International_phishing_campaign_EN-2.pdf
SMS message containing a phishing site (Fig. 3):
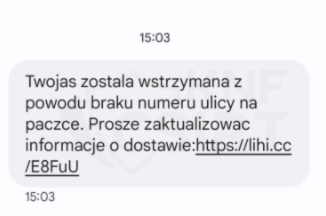
Figure 3 SMS message impersonating Polish Post Office
Phishing pages (fig. 4):
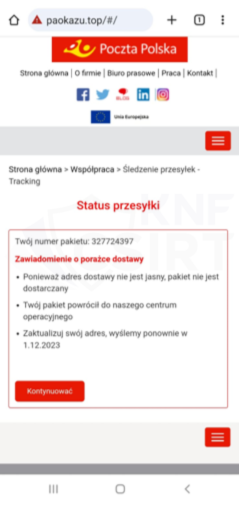
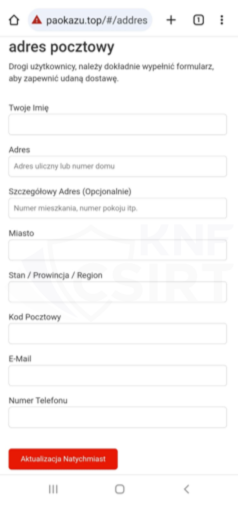
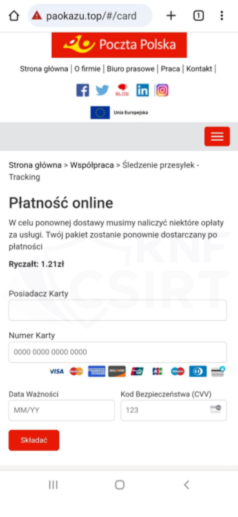
Figure 4 Phishing sites - impersonating Polish Post Office
Customs fee - again impersonating UPS
An identical campaign to the one we described in the November summary. Cybercriminals, impersonating UPS, sent out SMS messages informing about a package subject to a customs fee. To make the payment, recipients were instructed to click on an attached link, which in reality led to a phishing sit.
SMS message containing a phishing site (Fig. 5):
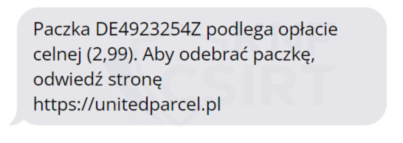
Figure 5 Fake SMS message impersonatin UPS
Phishing page (fig. 6):
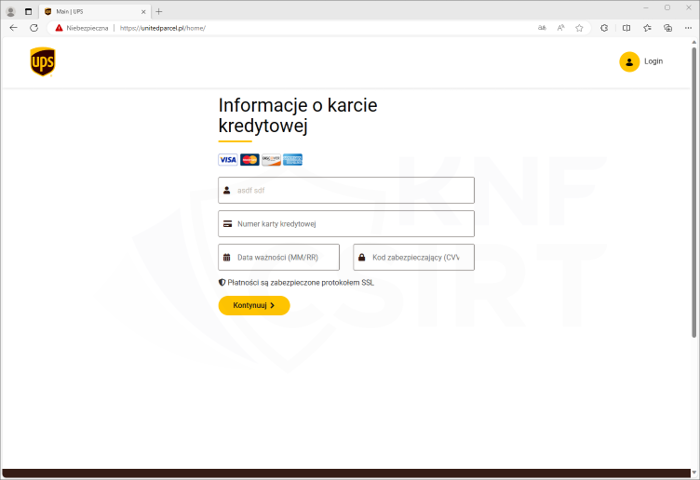
Figure 6 Phishing site - impersonating UPS
"Delivery failure", and again impersonating InPost
An identical campaign to the one we described in the November summary. Criminals, impersonating the courier company InPost, informed about an alleged necessity to update the address. The message contained a link, which, when clicked, led the victim to a phishing website. There, the criminals attempted to obtain credit card details, which they then used for fraudulent operations.
SMS message containing a phishing site (Fig. 7):
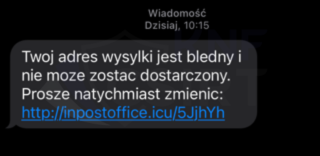
Figure 7 Fake SMS message - impersonating InPost
Phishing sites (Fig. 8):
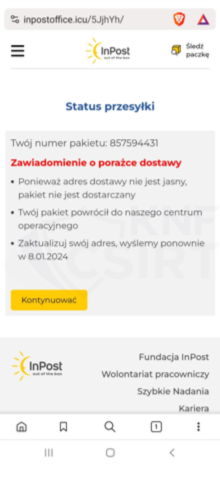
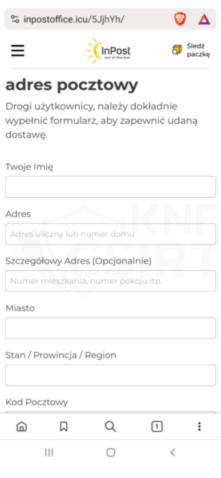
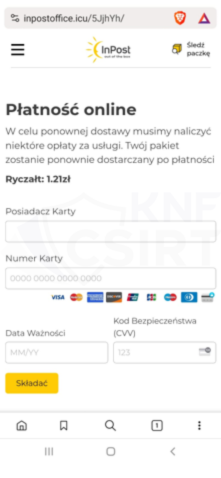
Figure 8 Phishing sites - impersonating InPost
Bank of points, so impersonating Bank PKO BP
Criminals, impersonating the bank PKO BP, sent out SMS messages. They informed about the necessity of exchanging points. The message contained a link, which, when clicked, led the victim to a phishing website. This site masqueraded as the Bank. There, the attackers tried to obtain credit card information.
SMS message containing a phishing site (Fig. 9):
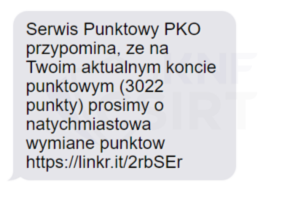
Figure 9 Fake SMS message - impersonating Bank PKO BP
Phishing sites (Fig. 10):
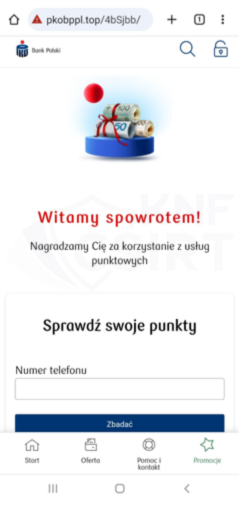
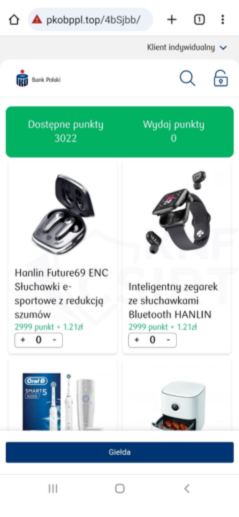
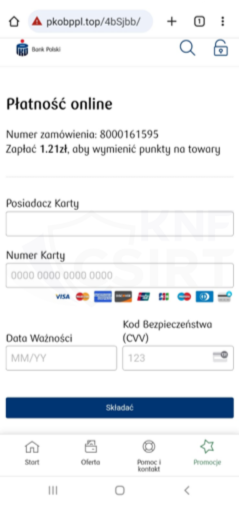
Figure 10 Phishing sites - impersonating Bank PKO BP
Receive ZTM card
Cybercriminals, impersonating ZTM (the Warsaw Public Transport Authority), announced a supposed opportunity to obtain a card that would entitle users to public transport rides. This card was advertised for sale at a very attractive price. After clicking on a link from the advertisement, the victim landed on a phishing site. There, they were presented with information about a supposed lottery. Subsequently, the victim was asked to enter their personal details and payment card information.
Advert on the Facebook platform, containing a phishing page (Fig. 11):

Figure 11 Fake ds - impersonating ZTM
Phishing sites, lottery and forms for entering personal data and credit card information (Fig. 12):

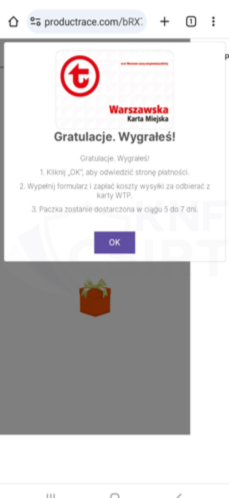
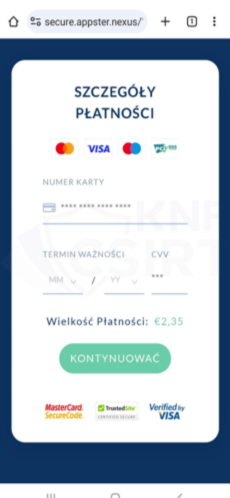
Figure 12 Phishing sites - impersonating ZTM
Price Deals
Cybercriminals offered products at competitive prices. On phishing sites, they impersonated well-know retail brands. Upon entering the site, the victim had to fill out a personal form. Then, the victim was asked to enter payment card details. All the data went into the hands of the criminals. This campaign had already been analyzed by us earlier, but now the criminals have changed the brand they are using.
Advert on the Facebook platform, containing a phishing page (Fig. 13):
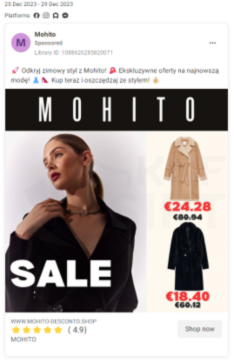
Figure 13 Fake ADS - impersonating well-know store
Phshing sites soliciting credit cards information (Fig. 14-16):
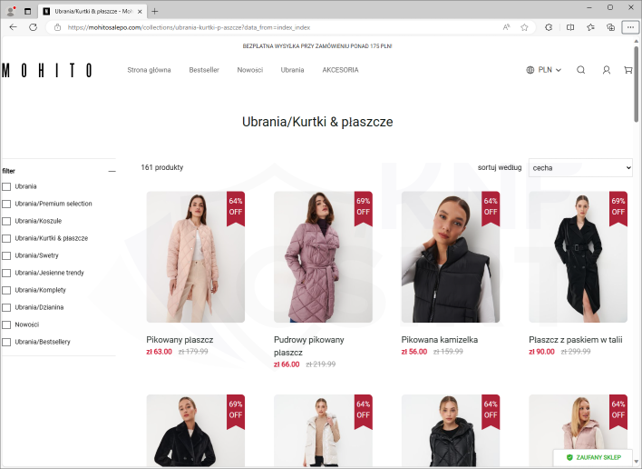
Figure 14 Phishing site - fake sale 1/3
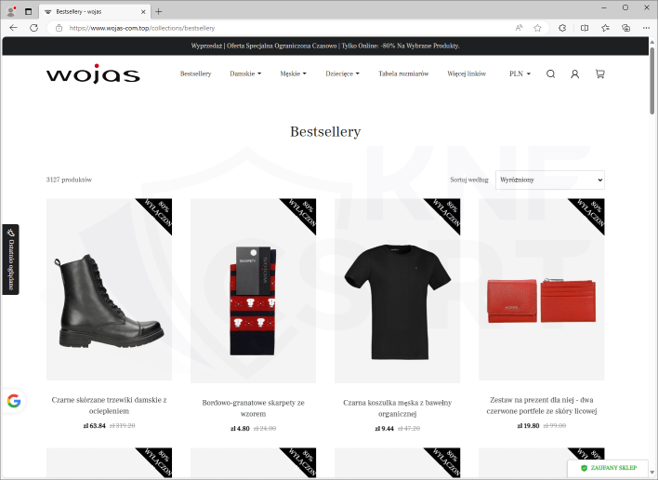
Figure 15 Phishing site - fake sale 2/3
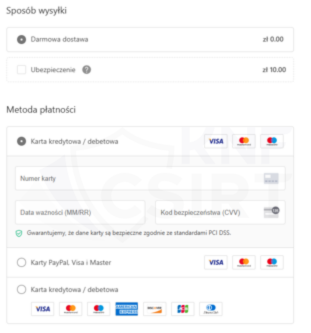
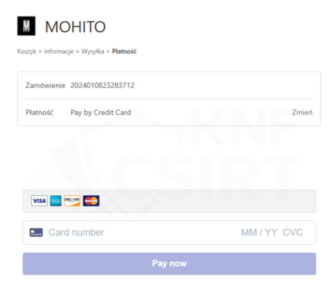
Figure 16 Phishing sites - fake sale, forms for entering credit cards information
Impersonating Booking
The attack on the clients of the Booking platform, already described in the November 2023 summary report, is still ongoing. Below, we remind you of the scheme of this crime.
How does it work?
- Hotel owners receive fake reservation inquiries in the form of email messages with malware.
- After infection, the criminals steal login data for Booking.
- They then create fake offers and phishing sites, deceiving hotel customers.
- The fake sites are sent to customers via Booking or other channels.
Message containing a phishing site (Fig. 17):
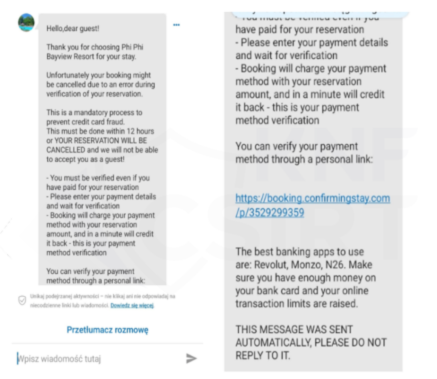
Figure 17 Fake message
Phishing site (Fig. 18):
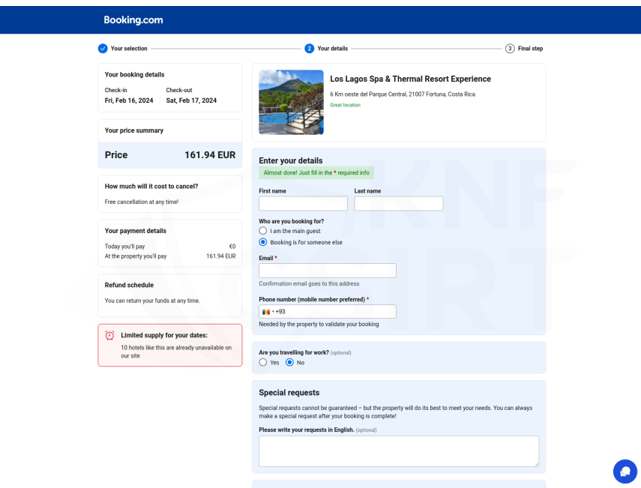
Figure 18 Phishing site - impersonating Booking
Yet another month of this year has demonstrated that criminals are constantly refining their methods of operation. We consistently believe that conducting informational and educational activities is crucial.
That's why news about cyber threats and fraudulent trends are also published on the following our social media platform: Twitter, LinkedIn and Facebook.

